Security researchers report a 40% increase in vulnerabilities found in Internet of Things devices during the past quarter. The findings highlight the critical importance of proper network segmentation and monitoring to protect smart home ecosystems from potential intrusions and data theft.
Alarming Rise in IoT Security Flaws
The latest cybersecurity research reveals a concerning trend in the smart home industry. As more households embrace connected devices, from smart thermostats to security cameras, the attack surface for cybercriminals continues to expand. The 40% quarterly increase in discovered vulnerabilities represents the highest surge recorded since comprehensive IoT monitoring began.
These vulnerabilities range from weak default passwords and unencrypted communications to firmware flaws that allow remote code execution. Many devices lack proper security updates, leaving homeowners exposed to potential breaches that could compromise their entire local network.
The Critical Role of Network Segmentation
Cybersecurity experts emphasize that implementing proper network segmentation is essential for maintaining a secure network environment. By isolating IoT devices on separate network segments, homeowners can prevent potential attackers from accessing critical systems and sensitive data stored on primary devices.
Key Protection Strategies:
- Create dedicated IoT network segments separate from main devices
- Implement robust firewall rules to control device communications
- Regular monitoring of network traffic for suspicious activities
- Ensure all devices receive timely security updates
- Change default passwords on all connected devices
Smart Home Ecosystem Risks
The interconnected nature of modern smart homes creates a complex web of potential entry points for malicious actors. A compromised smart doorbell or thermostat can serve as a gateway to access more sensitive devices on the same network, including computers containing personal financial information or business data.
Recent incidents have demonstrated how attackers exploit poorly secured IoT devices to launch larger-scale attacks, including distributed denial-of-service (DDoS) campaigns and cryptocurrency mining operations that can severely impact network performance and electricity costs.
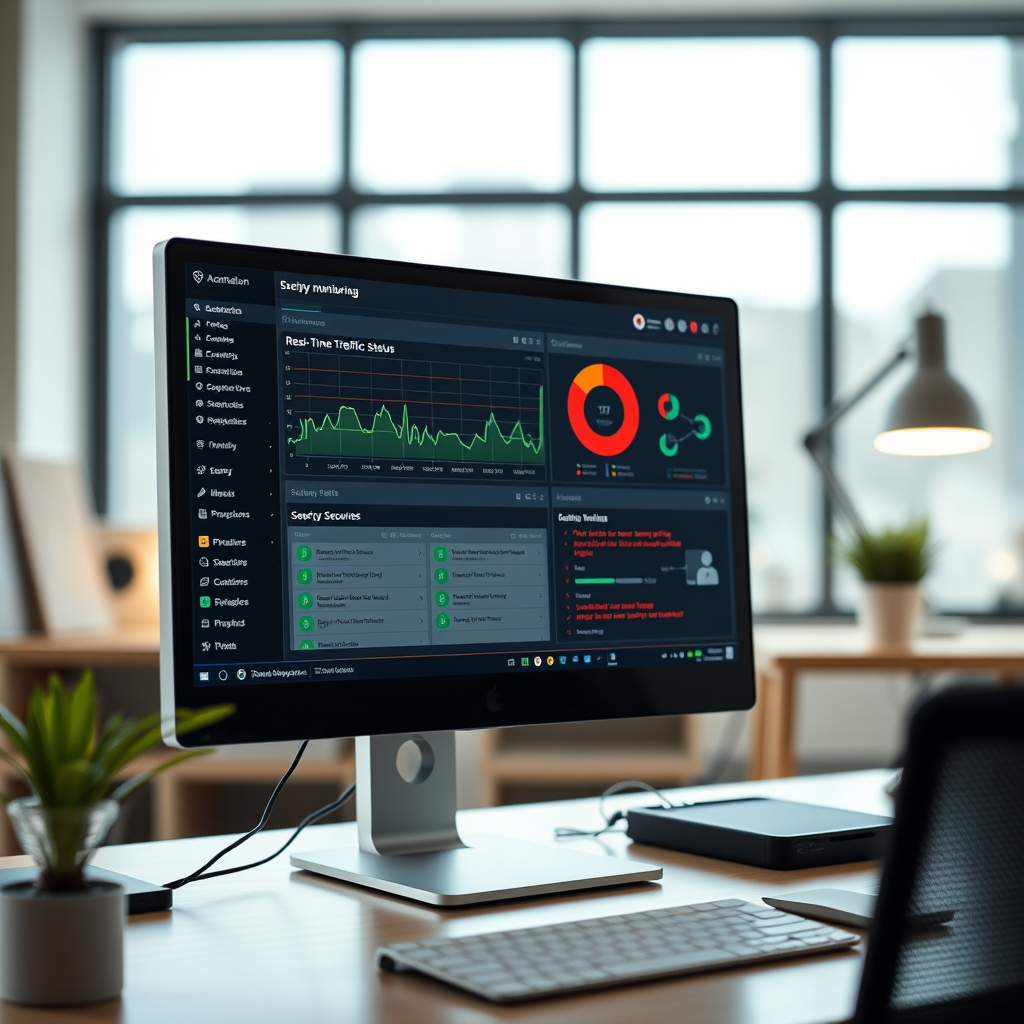
Proactive Monitoring and Response
Continuous monitoring of network activity has become indispensable for detecting potential security breaches before they escalate. Advanced monitoring solutions can identify unusual communication patterns, unauthorized access attempts, and suspicious data transfers that may indicate a compromised device.
Professional security services now offer specialized monitoring for smart home environments, providing real-time alerts and automated responses to potential threats. These services can quickly isolate compromised devices and prevent lateral movement within the network infrastructure.
Industry Response and Future Outlook
Major IoT manufacturers are beginning to implement more stringent security measures in response to growing concerns. New industry standards require devices to support automatic security updates, use strong encryption protocols, and provide clear security configuration options for end users.
However, experts warn that the rapid pace of smart home adoption continues to outpace security improvements. Consumers must take proactive steps to secure their connected devices and maintain vigilant monitoring of their home networks to protect against evolving cyber threats.
Security Recommendation
Homeowners with multiple IoT devices should consider implementing professional network security solutions that include device isolation, continuous monitoring, and automated threat response capabilities to maintain a truly secure local network environment.
